Netfilter
segunda-feira, 9 de dezembro de 2024
domingo, 12 de março de 2023
quinta-feira, 9 de julho de 2020
Turbinar navegação no Vivo Fibra
Uma maneira simples, para melhorar a navegação da internet, para usuários de Vivo_Fibra, é adicionando duas regrinhas de IPTables (funcionou , na HGU Askey RTF8115VW).
Nesse modem Askey, a empresa , fez um trabalho árduo em cima de Iptables, mas não visando uma melhor fluidez e desempenho do equipamento (que por sinal não é ruim), mas sim limitar o uso de portas específicas, e ter um controle maior, em cima dos três serviços ofertados.
Com o comando iptables-save > firewall, pode-se observar o seguinte:
*raw
:PREROUTING ACCEPT [1367542:113123572]
:OUTPUT ACCEPT [606361:59422162]
:GNT - [0:0]
:GNT_1_1 - [0:0]
:GNT_2_0 - [0:0]
-A PREROUTING -m mark --mark 0x8000/0x8000 -j GNT
-A GNT -d 178.128.171.12/32 -i ppp0 -j GNT_1_1
-A GNT -d 10.200.227.153/32 -i rbr2.2 -j GNT_1_1
-A GNT -d 192.168.15.1/32 -i rbr4.0 -j GNT_1_1
-A GNT_1_1 -p icmp -j ACCEPT
-A GNT_1_1 -p udp -m udp --dport 67 -j ACCEPT
-A GNT_1_1 -p udp -m udp --dport 53 -j ACCEPT
-A GNT_1_1 -p tcp -m tcp --dport 53 -j ACCEPT
-A GNT_1_1 -p tcp -m tcp --dport 8080 -j ACCEPT
-A GNT_1_1 -j DROP
-A GNT_2_0 -p icmp -j ACCEPT
-A GNT_2_0 -p udp -m udp --dport 67 -j ACCEPT
-A GNT_2_0 -p udp -m udp --dport 53 -j ACCEPT
-A GNT_2_0 -p tcp -m tcp --dport 53 -j ACCEPT
-A GNT_2_0 -j DROP
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*nat
:PREROUTING ACCEPT [411:39470]
:INPUT ACCEPT [15:948]
:OUTPUT ACCEPT [19:1292]
:POSTROUTING ACCEPT [0:0]
:DLB - [0:0]
:DLB_1_1 - [0:0]
:DLB_1_1_F_1 - [0:0]
:DLB_1_1_F_2 - [0:0]
:DLB_1_1_F_3 - [0:0]
:DLB_1_1_F_4 - [0:0]
:DLB_2_0 - [0:0]
:DNT - [0:0]
:DNT_1_1 - [0:0]
:DNT_1_1_F_1 - [0:0]
:DNT_1_1_F_2 - [0:0]
:DNT_1_1_F_3 - [0:0]
:DNT_1_1_F_4 - [0:0]
:DNT_1_1_H_P_1 - [0:0]
:DNT_1_1_H_P_2 - [0:0]
:DNT_1_1_H_P_3 - [0:0]
:DNT_1_1_H_P_4 - [0:0]
:DNT_1_1_H_P_F - [0:0]
:DNT_1_1_H_P_X - [0:0]
:DNT_1_1_H_R_1 - [0:0]
:DNT_1_1_H_R_2 - [0:0]
:DNT_1_1_H_R_3 - [0:0]
:DNT_1_1_H_R_4 - [0:0]
:DNT_1_1_H_R_F - [0:0]
:DNT_1_1_H_R_X - [0:0]
:DNT_1_1_H_X_1 - [0:0]
:DNT_1_1_H_X_2 - [0:0]
:DNT_1_1_H_X_3 - [0:0]
:DNT_1_1_H_X_4 - [0:0]
:DNT_1_1_H_X_F - [0:0]
:DNT_1_1_H_X_X - [0:0]
:DNT_1_1_X_P_1 - [0:0]
:DNT_1_1_X_P_2 - [0:0]
:DNT_1_1_X_P_3 - [0:0]
:DNT_1_1_X_P_4 - [0:0]
:DNT_1_1_X_P_F - [0:0]
:DNT_1_1_X_P_X - [0:0]
:DNT_1_1_X_R_1 - [0:0]
:DNT_1_1_X_R_2 - [0:0]
:DNT_1_1_X_R_3 - [0:0]
:DNT_1_1_X_R_4 - [0:0]
:DNT_1_1_X_R_F - [0:0]
:DNT_1_1_X_R_X - [0:0]
:DNT_1_1_X_X_1 - [0:0]
:DNT_1_1_X_X_2 - [0:0]
:DNT_1_1_X_X_3 - [0:0]
:DNT_1_1_X_X_4 - [0:0]
:DNT_1_1_X_X_F - [0:0]
:DNT_1_1_X_X_X - [0:0]
:DNT_2_0 - [0:0]
:DNT_2_0_H_P_F - [0:0]
:DNT_2_0_H_P_X - [0:0]
:DNT_2_0_H_R_F - [0:0]
:DNT_2_0_H_R_X - [0:0]
:DNT_2_0_H_X_F - [0:0]
:DNT_2_0_H_X_X - [0:0]
:DNT_2_0_X_P_F - [0:0]
:DNT_2_0_X_P_X - [0:0]
:DNT_2_0_X_R_F - [0:0]
:DNT_2_0_X_R_X - [0:0]
:DNT_2_0_X_X_F - [0:0]
:DNT_2_0_X_X_X - [0:0]
:IEX - [0:0]
:IEX_1_1 - [0:0]
:IEX_2_0 - [0:0]
:SHGW_PREROUTING - [0:0]
:SLB - [0:0]
:SLB_1_1 - [0:0]
:SLB_1_1_F_1 - [0:0]
:SLB_1_1_F_2 - [0:0]
:SLB_1_1_F_3 - [0:0]
:SLB_1_1_F_4 - [0:0]
:SLB_2_0 - [0:0]
:SNT - [0:0]
:SNT_1_1 - [0:0]
:SNT_2_0 - [0:0]
:TBR_M - [0:0]
:TBR_ME - [0:0]
:TBR_ME_1_1_F_1 - [0:0]
:TBR_ME_1_1_F_2 - [0:0]
:TBR_ME_1_1_F_3 - [0:0]
:TBR_ME_1_1_F_4 - [0:0]
:TBR_ME_1_1_L - [0:0]
:TBR_ME_1_1_W - [0:0]
:TBR_ME_2_0_L - [0:0]
:TBR_ME_2_0_W - [0:0]
:TBR_M_1_1_F_1 - [0:0]
:TBR_M_1_1_F_2 - [0:0]
:TBR_M_1_1_F_3 - [0:0]
:TBR_M_1_1_F_4 - [0:0]
:TBR_M_1_1_L - [0:0]
:TBR_M_1_1_W - [0:0]
:TBR_M_2_0_L - [0:0]
:TBR_M_2_0_W - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
-A PREROUTING -j IEX
-A PREROUTING -j TBR_ME
-A PREROUTING -p tcp -j DLB
-A PREROUTING -p tcp -j DNT
-A PREROUTING -p udp -j DLB
-A PREROUTING -p udp -j DNT
-A PREROUTING -p 33 -j DLB
-A PREROUTING -p 33 -j DNT
-A PREROUTING -p sctp -j DLB
-A PREROUTING -p sctp -j DNT
-A PREROUTING -j TBR_M
-A PREROUTING -j TEF_S
-A POSTROUTING -j SLB
-A POSTROUTING -j SNT
-A DLB -i rbr4.0 -j DLB_1_1
-A DLB_1_1 -d 178.238.171.12/32 -j DLB_1_1_F_2
-A DLB_1_1 -d 10.200.117.152/32 -j DLB_1_1_F_3
-A DLB_1_1 -d 192.168.15.1/32 -j DLB_1_1_F_1
-A DLB_1_1_F_1 -j DNT_1_1_H_P_1
-A DLB_1_1_F_1 -j DNT_1_1_H_P_X
-A DLB_1_1_F_1 -j DNT_1_1_H_R_1
-A DLB_1_1_F_1 -j DNT_1_1_H_R_X
-A DLB_1_1_F_1 -j DNT_1_1_H_X_1
-A DLB_1_1_F_1 -j DNT_1_1_H_X_X
-A DLB_1_1_F_1 -j DNT_1_1_X_P_1
-A DLB_1_1_F_1 -j DNT_1_1_X_P_X
-A DLB_1_1_F_1 -j DNT_1_1_X_R_1
-A DLB_1_1_F_1 -j DNT_1_1_X_R_X
-A DLB_1_1_F_1 -j DNT_1_1_X_X_1
-A DLB_1_1_F_1 -j DNT_1_1_X_X_X
-A DLB_1_1_F_2 -j DNT_1_1_H_P_2
-A DLB_1_1_F_2 -j DNT_1_1_H_P_X
-A DLB_1_1_F_2 -j DNT_1_1_H_R_2
-A DLB_1_1_F_2 -j DNT_1_1_H_R_X
-A DLB_1_1_F_2 -j DNT_1_1_H_X_2
-A DLB_1_1_F_2 -j DNT_1_1_H_X_X
-A DLB_1_1_F_2 -j DNT_1_1_X_P_2
-A DLB_1_1_F_2 -j DNT_1_1_X_P_X
-A DLB_1_1_F_2 -j DNT_1_1_X_R_2
-A DLB_1_1_F_2 -j DNT_1_1_X_R_X
-A DLB_1_1_F_2 -j DNT_1_1_X_X_2
-A DLB_1_1_F_2 -j DNT_1_1_X_X_X
-A DLB_1_1_F_3 -j DNT_1_1_H_P_3
-A DLB_1_1_F_3 -j DNT_1_1_H_P_X
-A DLB_1_1_F_3 -j DNT_1_1_H_R_3
-A DLB_1_1_F_3 -j DNT_1_1_H_R_X
-A DLB_1_1_F_3 -j DNT_1_1_H_X_3
-A DLB_1_1_F_3 -j DNT_1_1_H_X_X
-A DLB_1_1_F_3 -j DNT_1_1_X_P_3
-A DLB_1_1_F_3 -j DNT_1_1_X_P_X
-A DLB_1_1_F_3 -j DNT_1_1_X_R_3
-A DLB_1_1_F_3 -j DNT_1_1_X_R_X
-A DLB_1_1_F_3 -j DNT_1_1_X_X_3
-A DLB_1_1_F_3 -j DNT_1_1_X_X_X
-A DLB_1_1_F_4 -j DNT_1_1_H_P_4
-A DLB_1_1_F_4 -j DNT_1_1_H_P_X
-A DLB_1_1_F_4 -j DNT_1_1_H_R_4
-A DLB_1_1_F_4 -j DNT_1_1_H_R_X
-A DLB_1_1_F_4 -j DNT_1_1_H_X_4
-A DLB_1_1_F_4 -j DNT_1_1_H_X_X
-A DLB_1_1_F_4 -j DNT_1_1_X_P_4
-A DLB_1_1_F_4 -j DNT_1_1_X_P_X
-A DLB_1_1_F_4 -j DNT_1_1_X_R_4
-A DLB_1_1_F_4 -j DNT_1_1_X_R_X
-A DLB_1_1_F_4 -j DNT_1_1_X_X_4
-A DLB_1_1_F_4 -j DNT_1_1_X_X_X
-A DNT -i rbr2.2 -j DNT_1_1_F_3
-A DNT -i rbr3.3 -j DNT_1_1_F_4
-A DNT -i ppp0 -j DNT_1_1_F_2
-A DNT -i rbr4.0 -j DNT_1_1_F_1
-A DNT_1_1 -j DNT_1_1_H_P_F
-A DNT_1_1 -j DNT_1_1_H_P_X
-A DNT_1_1 -j DNT_1_1_H_R_F
-A DNT_1_1 -j DNT_1_1_H_R_X
-A DNT_1_1 -j DNT_1_1_H_X_F
-A DNT_1_1 -j DNT_1_1_H_X_X
-A DNT_1_1 -j DNT_1_1_X_P_F
-A DNT_1_1 -j DNT_1_1_X_P_X
-A DNT_1_1 -j DNT_1_1_X_R_F
-A DNT_1_1 -j DNT_1_1_X_R_X
-A DNT_1_1 -j DNT_1_1_X_X_F
-A DNT_1_1 -j DNT_1_1_X_X_X
-A DNT_1_1_F_1 -d 192.168.15.1/32 -j DNT_1_1
-A DNT_1_1_F_2 -d 178.238.171.12/32 -j DNT_1_1
-A DNT_1_1_F_3 -d 10.200.67.223/32 -j DNT_1_1
-A DNT_2_0 -j DNT_2_0_H_P_F
-A DNT_2_0 -j DNT_2_0_H_P_X
-A DNT_2_0 -j DNT_2_0_H_R_F
-A DNT_2_0 -j DNT_2_0_H_R_X
-A DNT_2_0 -j DNT_2_0_H_X_F
-A DNT_2_0 -j DNT_2_0_H_X_X
-A DNT_2_0 -j DNT_2_0_X_P_F
-A DNT_2_0 -j DNT_2_0_X_P_X
-A DNT_2_0 -j DNT_2_0_X_R_F
-A DNT_2_0 -j DNT_2_0_X_R_X
-A DNT_2_0 -j DNT_2_0_X_X_F
-A DNT_2_0 -j DNT_2_0_X_X_X
-A IEX -d 178.238.271.12/32 -i ppp0 -j IEX_1_1
-A IEX -d 10.20.227.153/32 -i rbr2.2 -j IEX_1_1
-A IEX -d 192.168.15.1/32 -i rbr4.0 -j IEX_1_1
-A IEX_1_1 -i ppp0 -p tcp -m tcp --dport 7547 -j ACCEPT
-A SLB -o rbr4.0 -j SLB_1_1_F_1
-A SLB_1_1 -o rbr2.2 -j MASQUERADE
-A SLB_1_1 -o rbr3.3 -j MASQUERADE
-A SLB_1_1 -o ppp0 -j MASQUERADE
-A SLB_1_1 -o rbr4.0 -j MASQUERADE
-A SLB_1_1_F_1 -s 192.168.15.0/24 -d 192.168.15.0/24 -j SLB_1_1
-A SLB_1_1_F_2 -s 178.238.171.12/32 -d 178.238.171.02/32 -j SLB_1_1
-A SLB_1_1_F_3 -s 10.22.136.0/20 -d 10.200.16.0/20 -j SLB_1_1
-A SNT -o rbr2.2 -j SNT_1_1
-A SNT -o rbr3.3 -j SNT_1_1
-A SNT -o ppp0 -j SNT_1_1
-A SNT_1_1 -o rbr2.2 -j MASQUERADE
-A SNT_1_1 -o rbr3.3 -j MASQUERADE
-A SNT_1_1 -o ppp0 -j MASQUERADE
-A TBR_M -d 178.238.171.12/32 -i ppp0 -j TBR_M_1_1_F_2
-A TBR_M -d 10.200.27.53/32 -i rbr2.2 -j TBR_M_1_1_F_3
-A TBR_M -d 192.168.15.1/32 -i rbr4.0 -j TBR_M_1_1_F_1
-A TBR_ME -d 178.138.171.12/32 -i ppp0 -j TBR_ME_1_1_F_2
-A TBR_ME -d 10.200.227.153/32 -i rbr2.2 -j TBR_ME_1_1_F_3
-A TBR_ME -d 192.168.15.1/32 -i rbr4.0 -j TBR_ME_1_1_F_1
-A TBR_ME_1_1_F_1 -j TBR_ME_1_1_L
-A TBR_ME_1_1_F_2 -j TBR_ME_1_1_W
-A TBR_ME_1_1_F_3 -j TBR_ME_1_1_W
-A TBR_ME_1_1_F_4 -j TBR_ME_1_1_W
-A TBR_ME_1_1_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_ME_1_1_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_ME_2_0_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_ME_2_0_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_1_1_F_1 -j TBR_M_1_1_L
-A TBR_M_1_1_F_2 -j TBR_M_1_1_W
-A TBR_M_1_1_F_3 -j TBR_M_1_1_W
-A TBR_M_1_1_F_4 -j TBR_M_1_1_W
-A TBR_M_1_1_L -p tcp -m tcp --dport 80 -j ACCEPT
-A TBR_M_1_1_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_M_1_1_L -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A TBR_M_1_1_W -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_1_1_W -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_1_1_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_L -p tcp -m tcp --dport 80 -j ACCEPT
-A TBR_M_2_0_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_M_2_0_L -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A TBR_M_2_0_W -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_2_0_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_W -p icmp -m icmp --icmp-type 8 -j RETURN
-A TEF_S -i rbr2.2 -j TEF_S_1_1
-A TEF_S -i rbr3.3 -j TEF_S_1_1
-A TEF_S -i ppp0 -j TEF_S_1_1
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j SHGW_PREROUTING
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*mangle
:PREROUTING ACCEPT [853:76347]
:INPUT ACCEPT [559:49150]
:FORWARD ACCEPT [101:8521]
:OUTPUT ACCEPT [721:93748]
:POSTROUTING ACCEPT [822:102269]
:QCL - [0:0]
:QCL_1_1_F_1 - [0:0]
:QCL_1_1_F_2 - [0:0]
:QCL_1_1_F_3 - [0:0]
:QCL_1_1_F_4 - [0:0]
:QCL_2_0_F_0 - [0:0]
:SHGW_PREROUTING - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
:TEF_S_1_1_WL - [0:0]
-A PREROUTING -j TEF_S
-A OUTPUT -j QCL
-A QCL -o rbr2.2 -j QCL_1_1_F_3
-A QCL -o rbr2.2 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o rbr3.3 -j QCL_1_1_F_4
-A QCL -o rbr3.3 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o ppp0 -j QCL_1_1_F_2
-A QCL -o ppp0 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o rbr4.0 -j QCL_1_1_F_1
-A QCL -o rbr4.0 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j TEF_S_1_1_WL
-A TEF_S_1_1 -p udp -m udp --dport 53 -j SHGW_PREROUTING
-A TEF_S_1_1 -p tcp -m tcp --dport 53 -j SHGW_PREROUTING
-A TEF_S_1_1_WL -d 172.29.130.5/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.6/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.5/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.6/32 -j ACCEPT
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*filter
:INPUT ACCEPT [119:11521]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [3559:444564]
:FIS - [0:0]
:FIS_L_1_1_R_0 - [0:0]
:FIS_L_2_0_R_1 - [0:0]
:FIS_W_1_1_R_0 - [0:0]
:FIS_W_2_0_R_1 - [0:0]
:FWL - [0:0]
:FWL_1_1 - [0:0]
:FWL_2_0 - [0:0]
:FWL_ADV_1_1_0 - [0:0]
:FWL_CHN_1_1_0 - [0:0]
:FWL_CHN_1_1_1 - [0:0]
:FWL_CHN_1_1_2 - [0:0]
:FWL_CHN_1_1_3 - [0:0]
:FWL_DEF - [0:0]
:FWL_HIGH - [0:0]
:FWL_LOW - [0:0]
:FWL_OFF - [0:0]
:IEX - [0:0]
:IEX_1_1 - [0:0]
:IEX_2_0 - [0:0]
:IPR - [0:0]
:MCL - [0:0]
:MCL_1_1 - [0:0]
:MCL_1_1_RULE - [0:0]
:MCL_2_0 - [0:0]
:MCL_2_0_RULE - [0:0]
:M_ETH - [0:0]
:M_WIFI_24G - [0:0]
:M_WIFI_5G - [0:0]
:OPR - [0:0]
:RIE - [0:0]
:SHGW_FORWARD - [0:0]
:TBR_M - [0:0]
:TBR_M_1_1_L - [0:0]
:TBR_M_1_1_SRC - [0:0]
:TBR_M_1_1_SRC_RULE - [0:0]
:TBR_M_1_1_W - [0:0]
:TBR_M_2_0_L - [0:0]
:TBR_M_2_0_SRC - [0:0]
:TBR_M_2_0_SRC_RULE - [0:0]
:TBR_M_2_0_W - [0:0]
:TEF_EI - [0:0]
:TEF_EI_1_1 - [0:0]
:TEF_EI_1_1_I - [0:0]
:TEF_EI_1_1_T - [0:0]
:TEF_EI_1_1_V - [0:0]
:TEF_EI_1_1_W - [0:0]
:TEF_EI_2_0 - [0:0]
:TEF_EI_2_0_I - [0:0]
:TEF_EI_2_0_T - [0:0]
:TEF_EI_2_0_V - [0:0]
:TEF_EI_2_0_W - [0:0]
:TEF_EO - [0:0]
:TEF_EO_1_1 - [0:0]
:TEF_EO_1_1_I - [0:0]
:TEF_EO_1_1_T - [0:0]
:TEF_EO_1_1_V - [0:0]
:TEF_EO_1_1_W - [0:0]
:TEF_EO_2_0 - [0:0]
:TEF_EO_2_0_I - [0:0]
:TEF_EO_2_0_T - [0:0]
:TEF_EO_2_0_V - [0:0]
:TEF_EO_2_0_W - [0:0]
:TEF_I - [0:0]
:TEF_I_1_1 - [0:0]
:TEF_I_1_1_I - [0:0]
:TEF_I_1_1_L - [0:0]
:TEF_I_1_1_LS - [0:0]
:TEF_I_1_1_W - [0:0]
:TEF_I_1_1_WS - [0:0]
:TEF_I_1_1_X - [0:0]
:TEF_I_2_0 - [0:0]
:TEF_I_2_0_I - [0:0]
:TEF_I_2_0_L - [0:0]
:TEF_I_2_0_LS - [0:0]
:TEF_I_2_0_W - [0:0]
:TEF_I_2_0_WS - [0:0]
:TEF_I_2_0_X - [0:0]
:TEF_O - [0:0]
:TEF_O_1_1 - [0:0]
:TEF_O_1_1_I - [0:0]
:TEF_O_1_1_L - [0:0]
:TEF_O_1_1_LS - [0:0]
:TEF_O_1_1_W - [0:0]
:TEF_O_1_1_WS - [0:0]
:TEF_O_1_1_X - [0:0]
:TEF_O_2_0 - [0:0]
:TEF_O_2_0_I - [0:0]
:TEF_O_2_0_L - [0:0]
:TEF_O_2_0_LS - [0:0]
:TEF_O_2_0_W - [0:0]
:TEF_O_2_0_WS - [0:0]
:TEF_O_2_0_X - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -j IEX
-A INPUT -j IPR
-A INPUT -j RIE
-A INPUT -j MCL
-A INPUT -j TBR_M
-A INPUT -j TEF_I
-A FORWARD -s 192.168.15.2/32 -j ACCEPT
-A FORWARD -d 192.168.15.2/32 -j ACCEPT
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x0/0xf0000000 -j M_WIFI_5G
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x50000000/0xf0000000 -j M_WIFI_24G
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x40000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x30000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x20000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x10000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -j FIS
-A FORWARD -j TEF_EI
-A FORWARD -j TEF_EO
-A FORWARD -j FWL
-A FORWARD -j TEF_I
-A FORWARD -j TEF_O
-A FORWARD -j TEF_S
-A OUTPUT -j TEF_O
-A OUTPUT -j OPR
-A FIS -i rbr2.2 -j FIS_W_1_1_R_0
-A FIS -i rbr3.3 -j FIS_W_1_1_R_0
-A FIS -i ppp0 -j FIS_W_1_1_R_0
-A FIS -i rbr4.0 -j FIS_L_1_1_R_0
-A FIS_L_1_1_R_0 -j RETURN
-A FIS_L_1_1_R_0 -o rbr4.0 -j DROP
-A FIS_L_2_0_R_1 -j RETURN
-A FIS_W_1_1_R_0
-A FIS_W_1_1_R_0 -o rbr2.2 -j DROP
-A FIS_W_1_1_R_0 -o rbr3.3 -j DROP
-A FIS_W_1_1_R_0 -o ppp0 -j DROP
-A FIS_W_2_0_R_1
-A FWL -i rbr2.2 -j FWL_1_1
-A FWL -i rbr3.3 -j FWL_1_1
-A FWL -i ppp0 -j FWL_1_1
-A FWL -i rbr4.0 -j FWL_1_1
-A FWL_1_1 -j FWL_DEF
-A FWL_1_1 -j FWL_ADV_1_1_0
-A FWL_2_0
-A FWL_2_0 -j FWL_OFF
-A FWL_ADV_1_1_0 -j FWL_CHN_1_1_0
-A FWL_ADV_1_1_0
-A FWL_ADV_1_1_0 -j RETURN
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr2.2
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr2.2 -j ACCEPT
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr3.3
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr3.3 -j ACCEPT
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_1
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_3
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_2
-A FWL_CHN_1_1_1
-A FWL_CHN_1_1_2
-A FWL_CHN_1_1_3
-A FWL_CHN_1_1_3 -i rbr4.0 -o ppp0
-A FWL_CHN_1_1_3 -i rbr4.0 -o ppp0 -j ACCEPT
-A FWL_CHN_1_1_3 -d 192.168.15.2/32 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 10:65535 --dport 10:65535
-A FWL_CHN_1_1_3 -d 192.168.15.2/32 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 10:65535 --dport 10:65535 -j ACCEPT
-A FWL_CHN_1_1_3 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 80 --dport 80
-A FWL_CHN_1_1_3 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 80 --dport 80 -j DROP
-A FWL_HIGH -p tcp -m tcp --dport 1:1023 -j RETURN
-A FWL_HIGH -p udp -m udp --dport 1:1023 -j RETURN
-A FWL_HIGH -p tcp -m tcp --dport 8080 -j RETURN
-A FWL_HIGH -p tcp -m tcp --dport 8443 -j RETURN
-A FWL_HIGH -p icmp -j RETURN
-A FWL_HIGH -j DROP
-A FWL_LOW -p tcp -m tcp --dport 1:1023 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1:1023 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1080 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1220 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1293 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1293 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1352 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1512 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1512 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1701 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1719 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1720 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1723 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1723 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1755 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1755 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1812:1813 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1812:1813 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1863 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1935 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2049 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2049 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2083 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2727 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2727 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2944 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2944 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3074 -j RETURN
-A FWL_LOW -p udp -m udp --dport 3074 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3260 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3478 -j RETURN
-A FWL_LOW -p udp -m udp --dport 3478 -j RETURN
-A FWL_LOW -p udp -m udp --dport 4500 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5060 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5060 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5061 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5190 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5349 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5353 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5800 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5900 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5900 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 6665:6669 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 8080 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 8443 -j RETURN
-A FWL_LOW -p icmp -j RETURN
-A FWL_LOW -j DROP
-A FWL_OFF -j RETURN
-A IEX -i rbr2.2 -j IEX_1_1
-A IEX -i rbr3.3 -j IEX_1_1
-A IEX -i ppp0 -j IEX_1_1
-A IEX -i rbr4.0 -j IEX_1_1
-A IEX_1_1 -i ppp0 -p tcp -m tcp --dport 7547 -j ACCEPT
-A IPR ! -p icmp -m state --state INVALID -j DROP
-A IPR -p icmp -m icmp --icmp-type 8 -m limit --limit 100/sec -j RETURN
-A IPR -p icmp -m icmp --icmp-type 8 -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 100/sec -j RETURN
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,PSH,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG SYN,PSH,ACK -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A IPR -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A IPR -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A IPR -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A MCL -i rbr2.2 -j MCL_1_1
-A MCL -i rbr3.3 -j MCL_1_1
-A MCL -i ppp0 -j MCL_1_1
-A MCL -i rbr4.0 -j MCL_1_1
-A MCL_1_1 -p tcp -m tcp --dport 80 -j RETURN
-A MCL_1_1 -p tcp -m tcp --dport 443 -j RETURN
-A MCL_1_1 -p tcp -m tcp --dport 23 -j DROP
-A MCL_1_1 -p tcp -m tcp --dport 22 -j RETURN
-A MCL_1_1_RULE -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 80 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 443 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 23 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 22 -j DROP
-A MCL_2_0_RULE -j DROP
-A M_ETH -m connlimit --connlimit-above 740 --connlimit-mask 32 -j DROP
-A M_WIFI_24G -m connlimit --connlimit-above 128 --connlimit-mask 32 -j DROP
-A M_WIFI_5G -m connlimit --connlimit-above 310 --connlimit-mask 32 -j DROP
-A OPR -p icmp -m icmp --icmp-type 3/3 -j DROP
-A RIE -i rbr2.2 -p icmp -m icmp --icmp-type 8 -j DROP
-A RIE -i rbr3.3 -p icmp -m icmp --icmp-type 8 -j DROP
-A RIE -i ppp0 -p icmp -m icmp --icmp-type 8 -j RETURN
-A RIE -i rbr4.0 -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M -i rbr2.2 -j TBR_M_1_1_W
-A TBR_M -i rbr3.3 -j TBR_M_1_1_W
-A TBR_M -i ppp0 -j TBR_M_1_1_W
-A TBR_M -i rbr4.0 -j TBR_M_1_1_L
-A TBR_M_1_1_L -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_1_1_L -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_1_1_L -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_1_1_SRC -j TBR_M_1_1_SRC_RULE
-A TBR_M_1_1_SRC -j ACCEPT
-A TBR_M_1_1_W -p tcp -m tcp --dport 80 -j DROP
-A TBR_M_1_1_W -p icmp -m icmp --icmp-type 8 -j DROP
-A TBR_M_1_1_W -p tcp -m tcp --dport 22 -j DROP
-A TBR_M_2_0_L -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_2_0_L -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_L -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_2_0_SRC -j TBR_M_2_0_SRC_RULE
-A TBR_M_2_0_SRC -j ACCEPT
-A TBR_M_2_0_W -p tcp -m tcp --dport 80 -j DROP
-A TBR_M_2_0_W -p tcp -m tcp --dport 22 -j DROP
-A TBR_M_2_0_W -p icmp -m icmp --icmp-type 8 -j DROP
-A TEF_EI -i rbr2.2 -j TEF_EI_1_1
-A TEF_EI -i rbr3.3 -j TEF_EI_1_1
-A TEF_EI -i ppp0 -j TEF_EI_1_1
-A TEF_EI -i rbr4.0 -j TEF_EI_1_1
-A TEF_EI_1_1 -i rbr3.3 -j TEF_EI_1_1_T
-A TEF_EI_1_1 -i rbr2.2 -j TEF_EI_1_1_V
-A TEF_EI_1_1 -i ppp0 -j TEF_EI_1_1_I
-A TEF_EI_1_1 -i rbr2.2 -j TEF_EI_1_1_W
-A TEF_EI_1_1 -i rbr3.3 -j TEF_EI_1_1_W
-A TEF_EI_1_1 -i ppp0 -j TEF_EI_1_1_W
-A TEF_EO -o rbr2.2 -j TEF_EO_1_1
-A TEF_EO -o rbr3.3 -j TEF_EO_1_1
-A TEF_EO -o ppp0 -j TEF_EO_1_1
-A TEF_EO -o rbr4.0 -j TEF_EO_1_1
-A TEF_EO_1_1 -o rbr3.3 -j TEF_EO_1_1_T
-A TEF_EO_1_1 -o rbr2.2 -j TEF_EO_1_1_V
-A TEF_EO_1_1 -o ppp0 -j TEF_EO_1_1_I
-A TEF_EO_1_1 -o rbr2.2 -j TEF_EO_1_1_W
-A TEF_EO_1_1 -o rbr3.3 -j TEF_EO_1_1_W
-A TEF_EO_1_1 -o ppp0 -j TEF_EO_1_1_W
-A TEF_I -i rbr2.2 -j TEF_I_1_1
-A TEF_I -i rbr3.3 -j TEF_I_1_1
-A TEF_I -i ppp0 -j TEF_I_1_1
-A TEF_I -i rbr4.0 -j TEF_I_1_1
-A TEF_I_1_1 -j TEF_I_1_1_I
-A TEF_I_1_1 -j TEF_I_1_1_LS
-A TEF_I_1_1 -j TEF_I_1_1_WS
-A TEF_I_1_1 -j TEF_I_1_1_X
-A TEF_I_1_1_LS -i rbr4.0 -j TEF_I_1_1_L
-A TEF_I_1_1_WS -i rbr2.2 -j TEF_I_1_1_W
-A TEF_I_1_1_WS -i rbr3.3 -j TEF_I_1_1_W
-A TEF_I_1_1_WS -i ppp0 -j TEF_I_1_1_W
-A TEF_I_2_0 -j TEF_I_2_0_I
-A TEF_I_2_0 -j TEF_I_2_0_LS
-A TEF_I_2_0 -j TEF_I_2_0_WS
-A TEF_I_2_0 -j TEF_I_2_0_X
-A TEF_O -o rbr2.2 -j TEF_O_1_1
-A TEF_O -o rbr3.3 -j TEF_O_1_1
-A TEF_O -o ppp0 -j TEF_O_1_1
-A TEF_O -o rbr4.0 -j TEF_O_1_1
-A TEF_O_1_1 -j TEF_O_1_1_I
-A TEF_O_1_1 -j TEF_O_1_1_LS
-A TEF_O_1_1 -j TEF_O_1_1_WS
-A TEF_O_1_1 -j TEF_O_1_1_X
-A TEF_O_1_1_LS -o rbr4.0 -j TEF_O_1_1_L
-A TEF_O_1_1_WS -o rbr2.2 -j TEF_O_1_1_W
-A TEF_O_1_1_WS -o rbr3.3 -j TEF_O_1_1_W
-A TEF_O_1_1_WS -o ppp0 -j TEF_O_1_1_W
-A TEF_O_2_0 -j TEF_O_2_0_I
-A TEF_O_2_0 -j TEF_O_2_0_LS
-A TEF_O_2_0 -j TEF_O_2_0_WS
-A TEF_O_2_0 -j TEF_O_2_0_X
-A TEF_S -i rbr2.2 -j TEF_S_1_1
-A TEF_S -i rbr3.3 -j TEF_S_1_1
-A TEF_S -i ppp0 -j TEF_S_1_1
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j SHGW_FORWARD
COMMIT
Para melhorar o desempenho da Internet, no geral, vamos adicionar duas regrinhas básicas a este Firewall.
Primeiro temos que acessar o modem, por SSH (costumo usar o putty):
o usuário é 'support' a senha é xxxyyyzzz (vem colado atrás do modem).
Para ter acesso ao sistema tecle 'sh'
Agora vamos inserir duas regras básicas:
#iptables -t mangle -I PREROUTING -i ppp0 -p udp --sport 53 --dport 1024:65535 -j ACCEPT
#iptables -t mangle -I PREROUTING 2 -i ppp0 -p tcp --sport 80:443 --dport 1024:65535 -j ACCEPT
Para visualizar as regras 'iptables -t mangle -nvL'
Regras adicionadas, estão passando os pacotes por elas.
O Speedtest:
Apesar do NIC ser USB, está com uma velocidade melhor.
O porém, lado ruim do negócio, jamais desligue o modem da tomada, pois as regras estão na memória RAM, vão sumir a cada novo BOOT, é bom usar um Nobreak. Para solucionar isso, teria que personalizar uma firmware especifica, como as da openwrt, isso é uma coisa bem complexa de ser feito. Se o modem desligar, necessita inserir as regras novamente.
Nesse modem Askey, a empresa , fez um trabalho árduo em cima de Iptables, mas não visando uma melhor fluidez e desempenho do equipamento (que por sinal não é ruim), mas sim limitar o uso de portas específicas, e ter um controle maior, em cima dos três serviços ofertados.
Com o comando iptables-save > firewall, pode-se observar o seguinte:
*raw
:PREROUTING ACCEPT [1367542:113123572]
:OUTPUT ACCEPT [606361:59422162]
:GNT - [0:0]
:GNT_1_1 - [0:0]
:GNT_2_0 - [0:0]
-A PREROUTING -m mark --mark 0x8000/0x8000 -j GNT
-A GNT -d 178.128.171.12/32 -i ppp0 -j GNT_1_1
-A GNT -d 10.200.227.153/32 -i rbr2.2 -j GNT_1_1
-A GNT -d 192.168.15.1/32 -i rbr4.0 -j GNT_1_1
-A GNT_1_1 -p icmp -j ACCEPT
-A GNT_1_1 -p udp -m udp --dport 67 -j ACCEPT
-A GNT_1_1 -p udp -m udp --dport 53 -j ACCEPT
-A GNT_1_1 -p tcp -m tcp --dport 53 -j ACCEPT
-A GNT_1_1 -p tcp -m tcp --dport 8080 -j ACCEPT
-A GNT_1_1 -j DROP
-A GNT_2_0 -p icmp -j ACCEPT
-A GNT_2_0 -p udp -m udp --dport 67 -j ACCEPT
-A GNT_2_0 -p udp -m udp --dport 53 -j ACCEPT
-A GNT_2_0 -p tcp -m tcp --dport 53 -j ACCEPT
-A GNT_2_0 -j DROP
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*nat
:PREROUTING ACCEPT [411:39470]
:INPUT ACCEPT [15:948]
:OUTPUT ACCEPT [19:1292]
:POSTROUTING ACCEPT [0:0]
:DLB - [0:0]
:DLB_1_1 - [0:0]
:DLB_1_1_F_1 - [0:0]
:DLB_1_1_F_2 - [0:0]
:DLB_1_1_F_3 - [0:0]
:DLB_1_1_F_4 - [0:0]
:DLB_2_0 - [0:0]
:DNT - [0:0]
:DNT_1_1 - [0:0]
:DNT_1_1_F_1 - [0:0]
:DNT_1_1_F_2 - [0:0]
:DNT_1_1_F_3 - [0:0]
:DNT_1_1_F_4 - [0:0]
:DNT_1_1_H_P_1 - [0:0]
:DNT_1_1_H_P_2 - [0:0]
:DNT_1_1_H_P_3 - [0:0]
:DNT_1_1_H_P_4 - [0:0]
:DNT_1_1_H_P_F - [0:0]
:DNT_1_1_H_P_X - [0:0]
:DNT_1_1_H_R_1 - [0:0]
:DNT_1_1_H_R_2 - [0:0]
:DNT_1_1_H_R_3 - [0:0]
:DNT_1_1_H_R_4 - [0:0]
:DNT_1_1_H_R_F - [0:0]
:DNT_1_1_H_R_X - [0:0]
:DNT_1_1_H_X_1 - [0:0]
:DNT_1_1_H_X_2 - [0:0]
:DNT_1_1_H_X_3 - [0:0]
:DNT_1_1_H_X_4 - [0:0]
:DNT_1_1_H_X_F - [0:0]
:DNT_1_1_H_X_X - [0:0]
:DNT_1_1_X_P_1 - [0:0]
:DNT_1_1_X_P_2 - [0:0]
:DNT_1_1_X_P_3 - [0:0]
:DNT_1_1_X_P_4 - [0:0]
:DNT_1_1_X_P_F - [0:0]
:DNT_1_1_X_P_X - [0:0]
:DNT_1_1_X_R_1 - [0:0]
:DNT_1_1_X_R_2 - [0:0]
:DNT_1_1_X_R_3 - [0:0]
:DNT_1_1_X_R_4 - [0:0]
:DNT_1_1_X_R_F - [0:0]
:DNT_1_1_X_R_X - [0:0]
:DNT_1_1_X_X_1 - [0:0]
:DNT_1_1_X_X_2 - [0:0]
:DNT_1_1_X_X_3 - [0:0]
:DNT_1_1_X_X_4 - [0:0]
:DNT_1_1_X_X_F - [0:0]
:DNT_1_1_X_X_X - [0:0]
:DNT_2_0 - [0:0]
:DNT_2_0_H_P_F - [0:0]
:DNT_2_0_H_P_X - [0:0]
:DNT_2_0_H_R_F - [0:0]
:DNT_2_0_H_R_X - [0:0]
:DNT_2_0_H_X_F - [0:0]
:DNT_2_0_H_X_X - [0:0]
:DNT_2_0_X_P_F - [0:0]
:DNT_2_0_X_P_X - [0:0]
:DNT_2_0_X_R_F - [0:0]
:DNT_2_0_X_R_X - [0:0]
:DNT_2_0_X_X_F - [0:0]
:DNT_2_0_X_X_X - [0:0]
:IEX - [0:0]
:IEX_1_1 - [0:0]
:IEX_2_0 - [0:0]
:SHGW_PREROUTING - [0:0]
:SLB - [0:0]
:SLB_1_1 - [0:0]
:SLB_1_1_F_1 - [0:0]
:SLB_1_1_F_2 - [0:0]
:SLB_1_1_F_3 - [0:0]
:SLB_1_1_F_4 - [0:0]
:SLB_2_0 - [0:0]
:SNT - [0:0]
:SNT_1_1 - [0:0]
:SNT_2_0 - [0:0]
:TBR_M - [0:0]
:TBR_ME - [0:0]
:TBR_ME_1_1_F_1 - [0:0]
:TBR_ME_1_1_F_2 - [0:0]
:TBR_ME_1_1_F_3 - [0:0]
:TBR_ME_1_1_F_4 - [0:0]
:TBR_ME_1_1_L - [0:0]
:TBR_ME_1_1_W - [0:0]
:TBR_ME_2_0_L - [0:0]
:TBR_ME_2_0_W - [0:0]
:TBR_M_1_1_F_1 - [0:0]
:TBR_M_1_1_F_2 - [0:0]
:TBR_M_1_1_F_3 - [0:0]
:TBR_M_1_1_F_4 - [0:0]
:TBR_M_1_1_L - [0:0]
:TBR_M_1_1_W - [0:0]
:TBR_M_2_0_L - [0:0]
:TBR_M_2_0_W - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
-A PREROUTING -j IEX
-A PREROUTING -j TBR_ME
-A PREROUTING -p tcp -j DLB
-A PREROUTING -p tcp -j DNT
-A PREROUTING -p udp -j DLB
-A PREROUTING -p udp -j DNT
-A PREROUTING -p 33 -j DLB
-A PREROUTING -p 33 -j DNT
-A PREROUTING -p sctp -j DLB
-A PREROUTING -p sctp -j DNT
-A PREROUTING -j TBR_M
-A PREROUTING -j TEF_S
-A POSTROUTING -j SLB
-A POSTROUTING -j SNT
-A DLB -i rbr4.0 -j DLB_1_1
-A DLB_1_1 -d 178.238.171.12/32 -j DLB_1_1_F_2
-A DLB_1_1 -d 10.200.117.152/32 -j DLB_1_1_F_3
-A DLB_1_1 -d 192.168.15.1/32 -j DLB_1_1_F_1
-A DLB_1_1_F_1 -j DNT_1_1_H_P_1
-A DLB_1_1_F_1 -j DNT_1_1_H_P_X
-A DLB_1_1_F_1 -j DNT_1_1_H_R_1
-A DLB_1_1_F_1 -j DNT_1_1_H_R_X
-A DLB_1_1_F_1 -j DNT_1_1_H_X_1
-A DLB_1_1_F_1 -j DNT_1_1_H_X_X
-A DLB_1_1_F_1 -j DNT_1_1_X_P_1
-A DLB_1_1_F_1 -j DNT_1_1_X_P_X
-A DLB_1_1_F_1 -j DNT_1_1_X_R_1
-A DLB_1_1_F_1 -j DNT_1_1_X_R_X
-A DLB_1_1_F_1 -j DNT_1_1_X_X_1
-A DLB_1_1_F_1 -j DNT_1_1_X_X_X
-A DLB_1_1_F_2 -j DNT_1_1_H_P_2
-A DLB_1_1_F_2 -j DNT_1_1_H_P_X
-A DLB_1_1_F_2 -j DNT_1_1_H_R_2
-A DLB_1_1_F_2 -j DNT_1_1_H_R_X
-A DLB_1_1_F_2 -j DNT_1_1_H_X_2
-A DLB_1_1_F_2 -j DNT_1_1_H_X_X
-A DLB_1_1_F_2 -j DNT_1_1_X_P_2
-A DLB_1_1_F_2 -j DNT_1_1_X_P_X
-A DLB_1_1_F_2 -j DNT_1_1_X_R_2
-A DLB_1_1_F_2 -j DNT_1_1_X_R_X
-A DLB_1_1_F_2 -j DNT_1_1_X_X_2
-A DLB_1_1_F_2 -j DNT_1_1_X_X_X
-A DLB_1_1_F_3 -j DNT_1_1_H_P_3
-A DLB_1_1_F_3 -j DNT_1_1_H_P_X
-A DLB_1_1_F_3 -j DNT_1_1_H_R_3
-A DLB_1_1_F_3 -j DNT_1_1_H_R_X
-A DLB_1_1_F_3 -j DNT_1_1_H_X_3
-A DLB_1_1_F_3 -j DNT_1_1_H_X_X
-A DLB_1_1_F_3 -j DNT_1_1_X_P_3
-A DLB_1_1_F_3 -j DNT_1_1_X_P_X
-A DLB_1_1_F_3 -j DNT_1_1_X_R_3
-A DLB_1_1_F_3 -j DNT_1_1_X_R_X
-A DLB_1_1_F_3 -j DNT_1_1_X_X_3
-A DLB_1_1_F_3 -j DNT_1_1_X_X_X
-A DLB_1_1_F_4 -j DNT_1_1_H_P_4
-A DLB_1_1_F_4 -j DNT_1_1_H_P_X
-A DLB_1_1_F_4 -j DNT_1_1_H_R_4
-A DLB_1_1_F_4 -j DNT_1_1_H_R_X
-A DLB_1_1_F_4 -j DNT_1_1_H_X_4
-A DLB_1_1_F_4 -j DNT_1_1_H_X_X
-A DLB_1_1_F_4 -j DNT_1_1_X_P_4
-A DLB_1_1_F_4 -j DNT_1_1_X_P_X
-A DLB_1_1_F_4 -j DNT_1_1_X_R_4
-A DLB_1_1_F_4 -j DNT_1_1_X_R_X
-A DLB_1_1_F_4 -j DNT_1_1_X_X_4
-A DLB_1_1_F_4 -j DNT_1_1_X_X_X
-A DNT -i rbr2.2 -j DNT_1_1_F_3
-A DNT -i rbr3.3 -j DNT_1_1_F_4
-A DNT -i ppp0 -j DNT_1_1_F_2
-A DNT -i rbr4.0 -j DNT_1_1_F_1
-A DNT_1_1 -j DNT_1_1_H_P_F
-A DNT_1_1 -j DNT_1_1_H_P_X
-A DNT_1_1 -j DNT_1_1_H_R_F
-A DNT_1_1 -j DNT_1_1_H_R_X
-A DNT_1_1 -j DNT_1_1_H_X_F
-A DNT_1_1 -j DNT_1_1_H_X_X
-A DNT_1_1 -j DNT_1_1_X_P_F
-A DNT_1_1 -j DNT_1_1_X_P_X
-A DNT_1_1 -j DNT_1_1_X_R_F
-A DNT_1_1 -j DNT_1_1_X_R_X
-A DNT_1_1 -j DNT_1_1_X_X_F
-A DNT_1_1 -j DNT_1_1_X_X_X
-A DNT_1_1_F_1 -d 192.168.15.1/32 -j DNT_1_1
-A DNT_1_1_F_2 -d 178.238.171.12/32 -j DNT_1_1
-A DNT_1_1_F_3 -d 10.200.67.223/32 -j DNT_1_1
-A DNT_2_0 -j DNT_2_0_H_P_F
-A DNT_2_0 -j DNT_2_0_H_P_X
-A DNT_2_0 -j DNT_2_0_H_R_F
-A DNT_2_0 -j DNT_2_0_H_R_X
-A DNT_2_0 -j DNT_2_0_H_X_F
-A DNT_2_0 -j DNT_2_0_H_X_X
-A DNT_2_0 -j DNT_2_0_X_P_F
-A DNT_2_0 -j DNT_2_0_X_P_X
-A DNT_2_0 -j DNT_2_0_X_R_F
-A DNT_2_0 -j DNT_2_0_X_R_X
-A DNT_2_0 -j DNT_2_0_X_X_F
-A DNT_2_0 -j DNT_2_0_X_X_X
-A IEX -d 178.238.271.12/32 -i ppp0 -j IEX_1_1
-A IEX -d 10.20.227.153/32 -i rbr2.2 -j IEX_1_1
-A IEX -d 192.168.15.1/32 -i rbr4.0 -j IEX_1_1
-A IEX_1_1 -i ppp0 -p tcp -m tcp --dport 7547 -j ACCEPT
-A SLB -o rbr4.0 -j SLB_1_1_F_1
-A SLB_1_1 -o rbr2.2 -j MASQUERADE
-A SLB_1_1 -o rbr3.3 -j MASQUERADE
-A SLB_1_1 -o ppp0 -j MASQUERADE
-A SLB_1_1 -o rbr4.0 -j MASQUERADE
-A SLB_1_1_F_1 -s 192.168.15.0/24 -d 192.168.15.0/24 -j SLB_1_1
-A SLB_1_1_F_2 -s 178.238.171.12/32 -d 178.238.171.02/32 -j SLB_1_1
-A SLB_1_1_F_3 -s 10.22.136.0/20 -d 10.200.16.0/20 -j SLB_1_1
-A SNT -o rbr2.2 -j SNT_1_1
-A SNT -o rbr3.3 -j SNT_1_1
-A SNT -o ppp0 -j SNT_1_1
-A SNT_1_1 -o rbr2.2 -j MASQUERADE
-A SNT_1_1 -o rbr3.3 -j MASQUERADE
-A SNT_1_1 -o ppp0 -j MASQUERADE
-A TBR_M -d 178.238.171.12/32 -i ppp0 -j TBR_M_1_1_F_2
-A TBR_M -d 10.200.27.53/32 -i rbr2.2 -j TBR_M_1_1_F_3
-A TBR_M -d 192.168.15.1/32 -i rbr4.0 -j TBR_M_1_1_F_1
-A TBR_ME -d 178.138.171.12/32 -i ppp0 -j TBR_ME_1_1_F_2
-A TBR_ME -d 10.200.227.153/32 -i rbr2.2 -j TBR_ME_1_1_F_3
-A TBR_ME -d 192.168.15.1/32 -i rbr4.0 -j TBR_ME_1_1_F_1
-A TBR_ME_1_1_F_1 -j TBR_ME_1_1_L
-A TBR_ME_1_1_F_2 -j TBR_ME_1_1_W
-A TBR_ME_1_1_F_3 -j TBR_ME_1_1_W
-A TBR_ME_1_1_F_4 -j TBR_ME_1_1_W
-A TBR_ME_1_1_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_ME_1_1_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_ME_2_0_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_ME_2_0_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_1_1_F_1 -j TBR_M_1_1_L
-A TBR_M_1_1_F_2 -j TBR_M_1_1_W
-A TBR_M_1_1_F_3 -j TBR_M_1_1_W
-A TBR_M_1_1_F_4 -j TBR_M_1_1_W
-A TBR_M_1_1_L -p tcp -m tcp --dport 80 -j ACCEPT
-A TBR_M_1_1_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_M_1_1_L -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A TBR_M_1_1_W -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_1_1_W -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_1_1_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_L -p tcp -m tcp --dport 80 -j ACCEPT
-A TBR_M_2_0_L -p tcp -m tcp --dport 22 -j ACCEPT
-A TBR_M_2_0_L -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A TBR_M_2_0_W -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_2_0_W -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_W -p icmp -m icmp --icmp-type 8 -j RETURN
-A TEF_S -i rbr2.2 -j TEF_S_1_1
-A TEF_S -i rbr3.3 -j TEF_S_1_1
-A TEF_S -i ppp0 -j TEF_S_1_1
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j SHGW_PREROUTING
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*mangle
:PREROUTING ACCEPT [853:76347]
:INPUT ACCEPT [559:49150]
:FORWARD ACCEPT [101:8521]
:OUTPUT ACCEPT [721:93748]
:POSTROUTING ACCEPT [822:102269]
:QCL - [0:0]
:QCL_1_1_F_1 - [0:0]
:QCL_1_1_F_2 - [0:0]
:QCL_1_1_F_3 - [0:0]
:QCL_1_1_F_4 - [0:0]
:QCL_2_0_F_0 - [0:0]
:SHGW_PREROUTING - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
:TEF_S_1_1_WL - [0:0]
-A PREROUTING -j TEF_S
-A OUTPUT -j QCL
-A QCL -o rbr2.2 -j QCL_1_1_F_3
-A QCL -o rbr2.2 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o rbr3.3 -j QCL_1_1_F_4
-A QCL -o rbr3.3 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o ppp0 -j QCL_1_1_F_2
-A QCL -o ppp0 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A QCL -o rbr4.0 -j QCL_1_1_F_1
-A QCL -o rbr4.0 -m mark --mark 0x0/0xffffe0f1 -j MARK --set-xmark 0x108/0x108
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j TEF_S_1_1_WL
-A TEF_S_1_1 -p udp -m udp --dport 53 -j SHGW_PREROUTING
-A TEF_S_1_1 -p tcp -m tcp --dport 53 -j SHGW_PREROUTING
-A TEF_S_1_1_WL -d 172.29.130.5/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.6/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.5/32 -j ACCEPT
-A TEF_S_1_1_WL -d 172.29.130.6/32 -j ACCEPT
COMMIT
# Completed on Fri Jul 3 19:46:36 2020
# Generated by iptables-save v1.4.20 on Fri Jul 3 19:46:36 2020
*filter
:INPUT ACCEPT [119:11521]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [3559:444564]
:FIS - [0:0]
:FIS_L_1_1_R_0 - [0:0]
:FIS_L_2_0_R_1 - [0:0]
:FIS_W_1_1_R_0 - [0:0]
:FIS_W_2_0_R_1 - [0:0]
:FWL - [0:0]
:FWL_1_1 - [0:0]
:FWL_2_0 - [0:0]
:FWL_ADV_1_1_0 - [0:0]
:FWL_CHN_1_1_0 - [0:0]
:FWL_CHN_1_1_1 - [0:0]
:FWL_CHN_1_1_2 - [0:0]
:FWL_CHN_1_1_3 - [0:0]
:FWL_DEF - [0:0]
:FWL_HIGH - [0:0]
:FWL_LOW - [0:0]
:FWL_OFF - [0:0]
:IEX - [0:0]
:IEX_1_1 - [0:0]
:IEX_2_0 - [0:0]
:IPR - [0:0]
:MCL - [0:0]
:MCL_1_1 - [0:0]
:MCL_1_1_RULE - [0:0]
:MCL_2_0 - [0:0]
:MCL_2_0_RULE - [0:0]
:M_ETH - [0:0]
:M_WIFI_24G - [0:0]
:M_WIFI_5G - [0:0]
:OPR - [0:0]
:RIE - [0:0]
:SHGW_FORWARD - [0:0]
:TBR_M - [0:0]
:TBR_M_1_1_L - [0:0]
:TBR_M_1_1_SRC - [0:0]
:TBR_M_1_1_SRC_RULE - [0:0]
:TBR_M_1_1_W - [0:0]
:TBR_M_2_0_L - [0:0]
:TBR_M_2_0_SRC - [0:0]
:TBR_M_2_0_SRC_RULE - [0:0]
:TBR_M_2_0_W - [0:0]
:TEF_EI - [0:0]
:TEF_EI_1_1 - [0:0]
:TEF_EI_1_1_I - [0:0]
:TEF_EI_1_1_T - [0:0]
:TEF_EI_1_1_V - [0:0]
:TEF_EI_1_1_W - [0:0]
:TEF_EI_2_0 - [0:0]
:TEF_EI_2_0_I - [0:0]
:TEF_EI_2_0_T - [0:0]
:TEF_EI_2_0_V - [0:0]
:TEF_EI_2_0_W - [0:0]
:TEF_EO - [0:0]
:TEF_EO_1_1 - [0:0]
:TEF_EO_1_1_I - [0:0]
:TEF_EO_1_1_T - [0:0]
:TEF_EO_1_1_V - [0:0]
:TEF_EO_1_1_W - [0:0]
:TEF_EO_2_0 - [0:0]
:TEF_EO_2_0_I - [0:0]
:TEF_EO_2_0_T - [0:0]
:TEF_EO_2_0_V - [0:0]
:TEF_EO_2_0_W - [0:0]
:TEF_I - [0:0]
:TEF_I_1_1 - [0:0]
:TEF_I_1_1_I - [0:0]
:TEF_I_1_1_L - [0:0]
:TEF_I_1_1_LS - [0:0]
:TEF_I_1_1_W - [0:0]
:TEF_I_1_1_WS - [0:0]
:TEF_I_1_1_X - [0:0]
:TEF_I_2_0 - [0:0]
:TEF_I_2_0_I - [0:0]
:TEF_I_2_0_L - [0:0]
:TEF_I_2_0_LS - [0:0]
:TEF_I_2_0_W - [0:0]
:TEF_I_2_0_WS - [0:0]
:TEF_I_2_0_X - [0:0]
:TEF_O - [0:0]
:TEF_O_1_1 - [0:0]
:TEF_O_1_1_I - [0:0]
:TEF_O_1_1_L - [0:0]
:TEF_O_1_1_LS - [0:0]
:TEF_O_1_1_W - [0:0]
:TEF_O_1_1_WS - [0:0]
:TEF_O_1_1_X - [0:0]
:TEF_O_2_0 - [0:0]
:TEF_O_2_0_I - [0:0]
:TEF_O_2_0_L - [0:0]
:TEF_O_2_0_LS - [0:0]
:TEF_O_2_0_W - [0:0]
:TEF_O_2_0_WS - [0:0]
:TEF_O_2_0_X - [0:0]
:TEF_S - [0:0]
:TEF_S_1_1 - [0:0]
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -j IEX
-A INPUT -j IPR
-A INPUT -j RIE
-A INPUT -j MCL
-A INPUT -j TBR_M
-A INPUT -j TEF_I
-A FORWARD -s 192.168.15.2/32 -j ACCEPT
-A FORWARD -d 192.168.15.2/32 -j ACCEPT
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x0/0xf0000000 -j M_WIFI_5G
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x50000000/0xf0000000 -j M_WIFI_24G
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x40000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x30000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x20000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -m mark --mark 0x10000000/0xf0000000 -j M_ETH
-A FORWARD -p tcp -m tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -j FIS
-A FORWARD -j TEF_EI
-A FORWARD -j TEF_EO
-A FORWARD -j FWL
-A FORWARD -j TEF_I
-A FORWARD -j TEF_O
-A FORWARD -j TEF_S
-A OUTPUT -j TEF_O
-A OUTPUT -j OPR
-A FIS -i rbr2.2 -j FIS_W_1_1_R_0
-A FIS -i rbr3.3 -j FIS_W_1_1_R_0
-A FIS -i ppp0 -j FIS_W_1_1_R_0
-A FIS -i rbr4.0 -j FIS_L_1_1_R_0
-A FIS_L_1_1_R_0 -j RETURN
-A FIS_L_1_1_R_0 -o rbr4.0 -j DROP
-A FIS_L_2_0_R_1 -j RETURN
-A FIS_W_1_1_R_0
-A FIS_W_1_1_R_0 -o rbr2.2 -j DROP
-A FIS_W_1_1_R_0 -o rbr3.3 -j DROP
-A FIS_W_1_1_R_0 -o ppp0 -j DROP
-A FIS_W_2_0_R_1
-A FWL -i rbr2.2 -j FWL_1_1
-A FWL -i rbr3.3 -j FWL_1_1
-A FWL -i ppp0 -j FWL_1_1
-A FWL -i rbr4.0 -j FWL_1_1
-A FWL_1_1 -j FWL_DEF
-A FWL_1_1 -j FWL_ADV_1_1_0
-A FWL_2_0
-A FWL_2_0 -j FWL_OFF
-A FWL_ADV_1_1_0 -j FWL_CHN_1_1_0
-A FWL_ADV_1_1_0
-A FWL_ADV_1_1_0 -j RETURN
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr2.2
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr2.2 -j ACCEPT
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr3.3
-A FWL_CHN_1_1_0 -i rbr4.0 -o rbr3.3 -j ACCEPT
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_1
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_3
-A FWL_CHN_1_1_0
-A FWL_CHN_1_1_0 -j FWL_CHN_1_1_2
-A FWL_CHN_1_1_1
-A FWL_CHN_1_1_2
-A FWL_CHN_1_1_3
-A FWL_CHN_1_1_3 -i rbr4.0 -o ppp0
-A FWL_CHN_1_1_3 -i rbr4.0 -o ppp0 -j ACCEPT
-A FWL_CHN_1_1_3 -d 192.168.15.2/32 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 10:65535 --dport 10:65535
-A FWL_CHN_1_1_3 -d 192.168.15.2/32 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 10:65535 --dport 10:65535 -j ACCEPT
-A FWL_CHN_1_1_3 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 80 --dport 80
-A FWL_CHN_1_1_3 -i ppp0 -o rbr4.0 -p tcp -m tcp --sport 80 --dport 80 -j DROP
-A FWL_HIGH -p tcp -m tcp --dport 1:1023 -j RETURN
-A FWL_HIGH -p udp -m udp --dport 1:1023 -j RETURN
-A FWL_HIGH -p tcp -m tcp --dport 8080 -j RETURN
-A FWL_HIGH -p tcp -m tcp --dport 8443 -j RETURN
-A FWL_HIGH -p icmp -j RETURN
-A FWL_HIGH -j DROP
-A FWL_LOW -p tcp -m tcp --dport 1:1023 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1:1023 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1080 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1220 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1293 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1293 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1352 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1512 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1512 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1701 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1719 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1720 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1723 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1723 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1755 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1755 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1812:1813 -j RETURN
-A FWL_LOW -p udp -m udp --dport 1812:1813 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1863 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 1935 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2049 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2049 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2083 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2727 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2727 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 2944 -j RETURN
-A FWL_LOW -p udp -m udp --dport 2944 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3074 -j RETURN
-A FWL_LOW -p udp -m udp --dport 3074 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3260 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 3478 -j RETURN
-A FWL_LOW -p udp -m udp --dport 3478 -j RETURN
-A FWL_LOW -p udp -m udp --dport 4500 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5060 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5060 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5061 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5190 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5349 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5353 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5800 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 5900 -j RETURN
-A FWL_LOW -p udp -m udp --dport 5900 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 6665:6669 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 8080 -j RETURN
-A FWL_LOW -p tcp -m tcp --dport 8443 -j RETURN
-A FWL_LOW -p icmp -j RETURN
-A FWL_LOW -j DROP
-A FWL_OFF -j RETURN
-A IEX -i rbr2.2 -j IEX_1_1
-A IEX -i rbr3.3 -j IEX_1_1
-A IEX -i ppp0 -j IEX_1_1
-A IEX -i rbr4.0 -j IEX_1_1
-A IEX_1_1 -i ppp0 -p tcp -m tcp --dport 7547 -j ACCEPT
-A IPR ! -p icmp -m state --state INVALID -j DROP
-A IPR -p icmp -m icmp --icmp-type 8 -m limit --limit 100/sec -j RETURN
-A IPR -p icmp -m icmp --icmp-type 8 -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 100/sec -j RETURN
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,PSH,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG SYN,PSH,ACK -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A IPR -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A IPR -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A IPR -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A IPR -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A MCL -i rbr2.2 -j MCL_1_1
-A MCL -i rbr3.3 -j MCL_1_1
-A MCL -i ppp0 -j MCL_1_1
-A MCL -i rbr4.0 -j MCL_1_1
-A MCL_1_1 -p tcp -m tcp --dport 80 -j RETURN
-A MCL_1_1 -p tcp -m tcp --dport 443 -j RETURN
-A MCL_1_1 -p tcp -m tcp --dport 23 -j DROP
-A MCL_1_1 -p tcp -m tcp --dport 22 -j RETURN
-A MCL_1_1_RULE -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 80 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 443 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 23 -j DROP
-A MCL_2_0 -p tcp -m tcp --dport 22 -j DROP
-A MCL_2_0_RULE -j DROP
-A M_ETH -m connlimit --connlimit-above 740 --connlimit-mask 32 -j DROP
-A M_WIFI_24G -m connlimit --connlimit-above 128 --connlimit-mask 32 -j DROP
-A M_WIFI_5G -m connlimit --connlimit-above 310 --connlimit-mask 32 -j DROP
-A OPR -p icmp -m icmp --icmp-type 3/3 -j DROP
-A RIE -i rbr2.2 -p icmp -m icmp --icmp-type 8 -j DROP
-A RIE -i rbr3.3 -p icmp -m icmp --icmp-type 8 -j DROP
-A RIE -i ppp0 -p icmp -m icmp --icmp-type 8 -j RETURN
-A RIE -i rbr4.0 -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M -i rbr2.2 -j TBR_M_1_1_W
-A TBR_M -i rbr3.3 -j TBR_M_1_1_W
-A TBR_M -i ppp0 -j TBR_M_1_1_W
-A TBR_M -i rbr4.0 -j TBR_M_1_1_L
-A TBR_M_1_1_L -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_1_1_L -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_1_1_L -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_1_1_SRC -j TBR_M_1_1_SRC_RULE
-A TBR_M_1_1_SRC -j ACCEPT
-A TBR_M_1_1_W -p tcp -m tcp --dport 80 -j DROP
-A TBR_M_1_1_W -p icmp -m icmp --icmp-type 8 -j DROP
-A TBR_M_1_1_W -p tcp -m tcp --dport 22 -j DROP
-A TBR_M_2_0_L -p tcp -m tcp --dport 80 -j RETURN
-A TBR_M_2_0_L -p tcp -m tcp --dport 22 -j RETURN
-A TBR_M_2_0_L -p icmp -m icmp --icmp-type 8 -j RETURN
-A TBR_M_2_0_SRC -j TBR_M_2_0_SRC_RULE
-A TBR_M_2_0_SRC -j ACCEPT
-A TBR_M_2_0_W -p tcp -m tcp --dport 80 -j DROP
-A TBR_M_2_0_W -p tcp -m tcp --dport 22 -j DROP
-A TBR_M_2_0_W -p icmp -m icmp --icmp-type 8 -j DROP
-A TEF_EI -i rbr2.2 -j TEF_EI_1_1
-A TEF_EI -i rbr3.3 -j TEF_EI_1_1
-A TEF_EI -i ppp0 -j TEF_EI_1_1
-A TEF_EI -i rbr4.0 -j TEF_EI_1_1
-A TEF_EI_1_1 -i rbr3.3 -j TEF_EI_1_1_T
-A TEF_EI_1_1 -i rbr2.2 -j TEF_EI_1_1_V
-A TEF_EI_1_1 -i ppp0 -j TEF_EI_1_1_I
-A TEF_EI_1_1 -i rbr2.2 -j TEF_EI_1_1_W
-A TEF_EI_1_1 -i rbr3.3 -j TEF_EI_1_1_W
-A TEF_EI_1_1 -i ppp0 -j TEF_EI_1_1_W
-A TEF_EO -o rbr2.2 -j TEF_EO_1_1
-A TEF_EO -o rbr3.3 -j TEF_EO_1_1
-A TEF_EO -o ppp0 -j TEF_EO_1_1
-A TEF_EO -o rbr4.0 -j TEF_EO_1_1
-A TEF_EO_1_1 -o rbr3.3 -j TEF_EO_1_1_T
-A TEF_EO_1_1 -o rbr2.2 -j TEF_EO_1_1_V
-A TEF_EO_1_1 -o ppp0 -j TEF_EO_1_1_I
-A TEF_EO_1_1 -o rbr2.2 -j TEF_EO_1_1_W
-A TEF_EO_1_1 -o rbr3.3 -j TEF_EO_1_1_W
-A TEF_EO_1_1 -o ppp0 -j TEF_EO_1_1_W
-A TEF_I -i rbr2.2 -j TEF_I_1_1
-A TEF_I -i rbr3.3 -j TEF_I_1_1
-A TEF_I -i ppp0 -j TEF_I_1_1
-A TEF_I -i rbr4.0 -j TEF_I_1_1
-A TEF_I_1_1 -j TEF_I_1_1_I
-A TEF_I_1_1 -j TEF_I_1_1_LS
-A TEF_I_1_1 -j TEF_I_1_1_WS
-A TEF_I_1_1 -j TEF_I_1_1_X
-A TEF_I_1_1_LS -i rbr4.0 -j TEF_I_1_1_L
-A TEF_I_1_1_WS -i rbr2.2 -j TEF_I_1_1_W
-A TEF_I_1_1_WS -i rbr3.3 -j TEF_I_1_1_W
-A TEF_I_1_1_WS -i ppp0 -j TEF_I_1_1_W
-A TEF_I_2_0 -j TEF_I_2_0_I
-A TEF_I_2_0 -j TEF_I_2_0_LS
-A TEF_I_2_0 -j TEF_I_2_0_WS
-A TEF_I_2_0 -j TEF_I_2_0_X
-A TEF_O -o rbr2.2 -j TEF_O_1_1
-A TEF_O -o rbr3.3 -j TEF_O_1_1
-A TEF_O -o ppp0 -j TEF_O_1_1
-A TEF_O -o rbr4.0 -j TEF_O_1_1
-A TEF_O_1_1 -j TEF_O_1_1_I
-A TEF_O_1_1 -j TEF_O_1_1_LS
-A TEF_O_1_1 -j TEF_O_1_1_WS
-A TEF_O_1_1 -j TEF_O_1_1_X
-A TEF_O_1_1_LS -o rbr4.0 -j TEF_O_1_1_L
-A TEF_O_1_1_WS -o rbr2.2 -j TEF_O_1_1_W
-A TEF_O_1_1_WS -o rbr3.3 -j TEF_O_1_1_W
-A TEF_O_1_1_WS -o ppp0 -j TEF_O_1_1_W
-A TEF_O_2_0 -j TEF_O_2_0_I
-A TEF_O_2_0 -j TEF_O_2_0_LS
-A TEF_O_2_0 -j TEF_O_2_0_WS
-A TEF_O_2_0 -j TEF_O_2_0_X
-A TEF_S -i rbr2.2 -j TEF_S_1_1
-A TEF_S -i rbr3.3 -j TEF_S_1_1
-A TEF_S -i ppp0 -j TEF_S_1_1
-A TEF_S -i rbr4.0 -j TEF_S_1_1
-A TEF_S_1_1 -j RETURN
-A TEF_S_1_1 -j SHGW_FORWARD
COMMIT
Para melhorar o desempenho da Internet, no geral, vamos adicionar duas regrinhas básicas a este Firewall.
Primeiro temos que acessar o modem, por SSH (costumo usar o putty):
o usuário é 'support' a senha é xxxyyyzzz (vem colado atrás do modem).
Para ter acesso ao sistema tecle 'sh'
Agora vamos inserir duas regras básicas:
#iptables -t mangle -I PREROUTING -i ppp0 -p udp --sport 53 --dport 1024:65535 -j ACCEPT
#iptables -t mangle -I PREROUTING 2 -i ppp0 -p tcp --sport 80:443 --dport 1024:65535 -j ACCEPT
Para visualizar as regras 'iptables -t mangle -nvL'
Regras adicionadas, estão passando os pacotes por elas.
O Speedtest:
Apesar do NIC ser USB, está com uma velocidade melhor.
O porém, lado ruim do negócio, jamais desligue o modem da tomada, pois as regras estão na memória RAM, vão sumir a cada novo BOOT, é bom usar um Nobreak. Para solucionar isso, teria que personalizar uma firmware especifica, como as da openwrt, isso é uma coisa bem complexa de ser feito. Se o modem desligar, necessita inserir as regras novamente.
segunda-feira, 4 de maio de 2020
VPN PPtP com Router Mikrotik e cliente Windows
Para ter acesso seguro a sua rede privada, de forma simples e rápida, usando um roteador Mikrotik.
Pense no seguinte cenário, a rede (remota) localizada numa pequena empresa, o usuário sem poder sair de casa, tem que acessar a rede da empresa onde trabalha, do seu computador, na sua casa. A forma mais fácil e rápida é criando uma VPN PPtP.
Configuração no router Mikrotik (roteador de borda com a internet):
Acesse a RB via WinBox e vá na aba 'PPP':
Vamos habilitar o protocolo PPTP:
Agora temos que criar um POOL (endereços IPs que serão entregues aos clientes):
Configure um range de IPs (rfc1918), válidos da sua rede interna:
Agora vem a configuração do 'PPP Profiles':
Preencha os campos com o nome, IP do Mikrotik e o POOL (range DHCP) criado:
Depois, vamos configurar o 'PPP Secret':
Coloque o nome da rede, a senha de acesso (senha do discador do windows), o serviço pptp e nome do Profile configurado anteriormente 'VPN':
Agora vamos a configuração do cliente Windows.
Vá em abrir central de Rede e compartilhamento:
Clique em configurar uma nova conexão ou rede:
Conectar a uma VPN:
Agora é preciso fornecer um ip público válido (conectado ao Mikrotik), um DNS dinâmico, que pode ser obtido através do cloud Mikrotik:
Para habilitar o DNS dinâmico do roteador Mikrotik, vá em IP e em 'cloud':
Depois é só preencher o nome de usuário (que foi configurado no PPP secret) e senha:
Se tudo estiver correto, a VPN PPtP funcionará:
No Roteador Mikrotik na aba PPP 'Active Connections' aparecerá a conexão VPN:
Para reforçar a segurança do Firewall e minimizar a lista de acessos indevidos (provavelmente todos os usuários terão IPs públicos dinâmicos para a conexão com a VPN)
# Bloqueio de IPs
/ip firewall address-list
add list="block_ip" address=100.64.0.0/10
add list="block_ip" address=169.254.0.0/16
add list="block_ip" address=192.0.0.0/24
add list="block_ip" address=192.0.2.0/24
add list="block_ip" address=198.18.0.0/15
add list="block_ip" address=198.51.100.0/24
add list="block_ip" address=203.0.113.0/24
add list="block_ip" address=224.0.0.0/3
add list="block_ip" address=104.244.42.0/24
add list="block_ip" address=172.217.28.0/18
add list="block_ip" address=66.45.237.219
add list="block_ip" address=192.16.58.8
add list="block_ip" address=192.16.59.1
add list="block_ip" address=151.101.129.44
add list="block_ip" address=151.101.1.44
add list="block_ip" address=151.101.93.44
add list="block_ip" address=151.101.193.44
add list="block_ip" address=167.99.229.185
add list="block_ip" address=200.152.162.136/30
add list="block_ip" address=200.152.162.189
add list="block_ip" address=201.6.48.13
add list="block_ip" address=201.6.52.66
add list="block_ip" address=191.180.43.215
add list="block_ip" address=179.153.108.148
add list="block_ip" address=186.204.215.58
add list="block_ip" address=186.204.29.230
add list="block_ip" address=189.120.72.203
add list="block_ip" address=189.120.76.139
add list="block_ip" address=189.33.66.238
add list="block_ip" address=189.33.67.119
add list="block_ip" address=189.62.238.248
add list="block_ip" address=177.32.85.38
add list="block_ip" address=177.33.174.218
add list="block_ip" address=177.81.70.237
add list="block_ip" address=177.81.78.103
#Lista de IPs Válidos para o Brasil
add address=177.0.0.0/8 list=brip
add address=191.0.0.0/8 list=brip
add address=200.0.0.0/8 list=brip
add address=201.0.0.0/8 list=brip
add address=179.0.0.0/8 list=brip
add address=186.0.0.0/8 list=brip
add address=189.0.0.0/8 list=brip
/ip firewall filter
add action=drop chain=input comment="#Bloqueio pela Address List" \
in-interface="bridge1" limit=1,2:packet log=yes log-prefix=\
"Log_to_Block_ip_Address Lists" src-address-list=block_ip
add action=accept chain=input dst-port=1723 in-interface=bridge1 \
limit=1,1:packet log=yes log-prefix="\"VPN_acesso_autorizado_IP:\
"" protocol=tcp src-address-list=brip
add action=add-src-to-address-list address-list=port:1723 \
address-list-timeout=1m chain=input dst-port=1723 protocol=tcp
/ip firewall raw
add action=drop chain=prerouting disabled=yes dst-port=1723 \
in-interface=bridge1 log=yes log-prefix="\"#DROP_IPs_VPN:\
""protocol=tcp src-address-list=!brip
#Copie as regras no Terminal do router Mikrotik, no WinBox, ou via SSH, pelo Putty.
Pense no seguinte cenário, a rede (remota) localizada numa pequena empresa, o usuário sem poder sair de casa, tem que acessar a rede da empresa onde trabalha, do seu computador, na sua casa. A forma mais fácil e rápida é criando uma VPN PPtP.
Configuração no router Mikrotik (roteador de borda com a internet):
Acesse a RB via WinBox e vá na aba 'PPP':
Vamos habilitar o protocolo PPTP:
Agora temos que criar um POOL (endereços IPs que serão entregues aos clientes):
Configure um range de IPs (rfc1918), válidos da sua rede interna:
Agora vem a configuração do 'PPP Profiles':
Preencha os campos com o nome, IP do Mikrotik e o POOL (range DHCP) criado:
Depois, vamos configurar o 'PPP Secret':
Coloque o nome da rede, a senha de acesso (senha do discador do windows), o serviço pptp e nome do Profile configurado anteriormente 'VPN':
Agora vamos a configuração do cliente Windows.
Vá em abrir central de Rede e compartilhamento:
Clique em configurar uma nova conexão ou rede:
Conectar a uma VPN:
Agora é preciso fornecer um ip público válido (conectado ao Mikrotik), um DNS dinâmico, que pode ser obtido através do cloud Mikrotik:
Para habilitar o DNS dinâmico do roteador Mikrotik, vá em IP e em 'cloud':
Depois é só preencher o nome de usuário (que foi configurado no PPP secret) e senha:
Se tudo estiver correto, a VPN PPtP funcionará:
No Roteador Mikrotik na aba PPP 'Active Connections' aparecerá a conexão VPN:
Para reforçar a segurança do Firewall e minimizar a lista de acessos indevidos (provavelmente todos os usuários terão IPs públicos dinâmicos para a conexão com a VPN)
# Bloqueio de IPs
/ip firewall address-list
add list="block_ip" address=100.64.0.0/10
add list="block_ip" address=169.254.0.0/16
add list="block_ip" address=192.0.0.0/24
add list="block_ip" address=192.0.2.0/24
add list="block_ip" address=198.18.0.0/15
add list="block_ip" address=198.51.100.0/24
add list="block_ip" address=203.0.113.0/24
add list="block_ip" address=224.0.0.0/3
add list="block_ip" address=104.244.42.0/24
add list="block_ip" address=172.217.28.0/18
add list="block_ip" address=66.45.237.219
add list="block_ip" address=192.16.58.8
add list="block_ip" address=192.16.59.1
add list="block_ip" address=151.101.129.44
add list="block_ip" address=151.101.1.44
add list="block_ip" address=151.101.93.44
add list="block_ip" address=151.101.193.44
add list="block_ip" address=167.99.229.185
add list="block_ip" address=200.152.162.136/30
add list="block_ip" address=200.152.162.189
add list="block_ip" address=201.6.48.13
add list="block_ip" address=201.6.52.66
add list="block_ip" address=191.180.43.215
add list="block_ip" address=179.153.108.148
add list="block_ip" address=186.204.215.58
add list="block_ip" address=186.204.29.230
add list="block_ip" address=189.120.72.203
add list="block_ip" address=189.120.76.139
add list="block_ip" address=189.33.66.238
add list="block_ip" address=189.33.67.119
add list="block_ip" address=189.62.238.248
add list="block_ip" address=177.32.85.38
add list="block_ip" address=177.33.174.218
add list="block_ip" address=177.81.70.237
add list="block_ip" address=177.81.78.103
#Lista de IPs Válidos para o Brasil
add address=177.0.0.0/8 list=brip
add address=191.0.0.0/8 list=brip
add address=200.0.0.0/8 list=brip
add address=201.0.0.0/8 list=brip
add address=179.0.0.0/8 list=brip
add address=186.0.0.0/8 list=brip
add address=189.0.0.0/8 list=brip
/ip firewall filter
add action=drop chain=input comment="#Bloqueio pela Address List" \
in-interface="bridge1" limit=1,2:packet log=yes log-prefix=\
"Log_to_Block_ip_Address Lists" src-address-list=block_ip
add action=accept chain=input dst-port=1723 in-interface=bridge1 \
limit=1,1:packet log=yes log-prefix="\"VPN_acesso_autorizado_IP:\
"" protocol=tcp src-address-list=brip
add action=add-src-to-address-list address-list=port:1723 \
address-list-timeout=1m chain=input dst-port=1723 protocol=tcp
/ip firewall raw
add action=drop chain=prerouting disabled=yes dst-port=1723 \
in-interface=bridge1 log=yes log-prefix="\"#DROP_IPs_VPN:\
""protocol=tcp src-address-list=!brip
#Copie as regras no Terminal do router Mikrotik, no WinBox, ou via SSH, pelo Putty.
sexta-feira, 1 de maio de 2020
Exportar Logs do Mikrotik para o Linux Server
Para desenvolver um bom Firewall, em qualquer plataforma, é essencial a visualização de Logs, dos acessos à rede como um todo. Nas RB's Mikrotik, a quantidade de memória, tanto a memória volátil, quanto a memória não volátil, tem quantidades limitadas. Hoje em dia qualquer Server Linux (X86), tem de sobra, memória Ram e de armazenamento.
A solução é repassar os Logs das RBs para o HD de um Servidor Linux, isso é bem simples, apenas editando um arquivo de configuração:
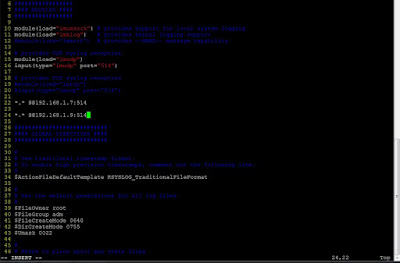
#vim /etc/rsyslog.conf
Descomente as linhas:
module(load="imudp")
input(type="imudp" port="514")
Desse modo será usado a porta udp 514 para a troca de dados (logs) entre os dispositivos.
Adicione a linha:
*.* @@192.168.1.7:514
*.* @@192.168.1.9:514
Esses são os Ips das RBs Mikrotik.
Depois de tudo configurado, rode o comando:
#systemctl restart rsyslog
Agora a configuração nas RBs:
Para visualização dos Logs no Servidor Linux:
#tail -f /var/log/messages
A visualização de Logs em tempo real, sem saturar a memória ram das RBs Mikrotik.
Para assegurar acesso as informações de Logs do Sistema, apenas aos micros da rede interna:
quinta-feira, 26 de março de 2020
Netfilter on Mikrotik Router
Transpondo regras de Firewall IPtables para o Mikrotik:
#Interfaces:
bridge1=Lan
ether6=Wan
#Regras Básicas de Acesso:
iptables -A FORWARD -i bridge1 -o ether6 -p tcp -s 192.168.1.0/27 -d 0/0 --sport 1024:65535 --dport 0:1024 -j ACCEPT
iptables -A FORWARD -i ether6 -o bridge1 -p tcp -s 0/0 -d 192.168.1.0/27 --sport 0:1024 --dport 1024:65535 -j ACCEPT
#Estas duas regras são bem completas, por si só, já liberam a maioria dos serviços de acesso à rede que utiliza portas tcp, com segurança.
iptables -A INPUT -i ether6 -p udp -s 200.160.7.186 --sport 123 --dport 123 -j ACCEPT
#Esta regra libera acesso ao Servidor NTP, para consulta do Horário.
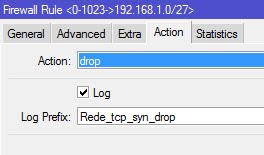
iptables -A FORWARD -i ether6 -o bridge1 -d 192.168.1.0/27 -p tcp --sport 0:1023 -m state --state NEW -j DROP
iptables -A FORWARD -i ether6 -o bridge1 -d 192.168.1.0/27 -p tcp --sport 0:1023 -m state --state NEW - -j LOG --log-prefix "Rede_tcp_syn_drop"
#Esta regra protege a rede do início de acessos indevidos pelas portas tcp baixas. Depois da ação, é gravado o LOG, com o prefixo "Rede_tcp_syn_drop".
iptables -A INPUT -i ether6 -p udp --dport 0:1024 -j DROP
#Esta regra bloqueia tentativas de acesso à portas UDP baixas.
#Libere antes desta regra, os acessos mais comuns às portas UDP, como DNS e NTP.
Assinar:
Comentários (Atom)